A brief note on security:
- ECC security is Transaction based security.
- HR security is position based security.
- BW/BI is Query based security.
- Data in ECC system is permanent data. where as BW/BI is analytics data.
Ex1: bank transaction data for all the transaction will be stored bank server is an example for ECC system data.where as last 6 transaction data which, will get in mini statement is query based data from BW/BI server.
Ex2: Suppose their are 3 lakhs of employee working in an ERP based company.this data will be stored in ECC systems. where as query for top 10 salary getting employees query will be in BW/BI system.
- Query in BW/BI server will re-arrange the data in ECC system.
- Authorization maintenance for this queries is called BW/BI security.
connection between ECC system to BW/BI system will be done through RFC connection. with the concept behind it ETL tool.
E - extract.
T- Translation.
L- Load.
E - extract.
T- Translation.
L- Load.
ex: in ECC system in BI/BW system
emp name ----------------------------------------------------------------> first name
Difference between BW and BI systems:
----------------------------------------------------------|---------------------------------------------------------------
BW BI
------------------------------------------------------------------------------------------------------------------------
- last version of BW - 3.5 last version of BI 7.X
- ABAP based Netweaver based
- Customizing authorization objects Analysis authorization
- T-code: RSSM T-code: RSECADMIN
- one authorization objects have 10 fields No limit
--------------------------------------------------------------------------------------------------------------------------
Note:
for security admin only works on 2 T-codes: RSSM (if the system is BW system.)
RSECADMIN (if the system is BI system.)
for security admin only works on 2 T-codes: RSSM (if the system is BW system.)
RSECADMIN (if the system is BI system.)
Key points to be consider for BI security:
- source system: It's either SAP or NON SAP system.
- Data source: whatever the data available in SAP BI system we call Data source (Info packages).
- Info Area: the place where BI data is store in the BI system is called INFO AREA(folder name).
- Info object catalog: who folds actual /all objects( Folders inside INFO AREA, for better segregation).
eg: Movies is folder name, inside telugu movies,tamil movies,Kanada movies are folders inside the folder Movies.
- Info objects: Each field in the tables( combination of key figures and characteristics)
- Info provider: Through info provider will load the data inti info objects.
Here we go for the practical steps 👀:
- login to BI system.by providing user id and password.
2. Access T-code RSECADMIN
5.Enter the Authorization object name.So called as Role in ECC systems.
6.click on create.
7.provide the description details.
8.click on insert special characters to obtain default authorization object.
8(2). Resultant screen for the step 8.
9. click on the intervel option.as shown below.
10.Click on the add button. To add the custom role as per the business requirement.
11.Then click on the help button. As shown below to add Info objects.
12. Add the required info object.
13. Add the intervals value.
14. Click on SAVE.
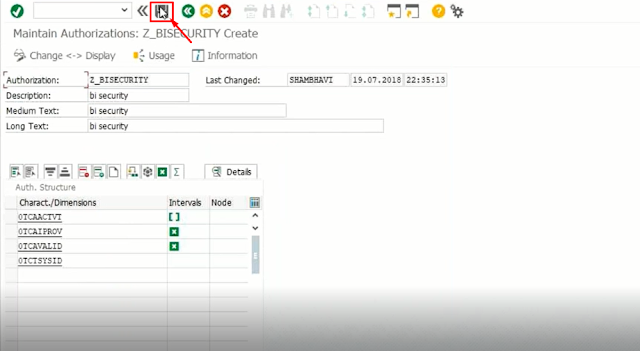
14. To add no. of info objects
15. Followed by operator value.
16. select the value as per the business requirement.
19. finally SAVE again, after defining the interval value.

20.From the previous steps creation of Authorization required is completed. Now assign to user.
21.Click on Assign.
22.Click on Change as shown below screenshot.
23. Enter the Authorization role in the Authorization selections & click on Insert.
Cross check the result as shown in the screen shot as 2.
Hurrah!!! the authorization is added to the user in BI system.
Authorization maintenance for BW(3.5) system
Note: The authorization maintenance for BW system is almost similar to ECC system. But the below authorization object need to add manually.
step 1:
SU01 ---> collection user details--> assign the T-code: RSSM
PFCFG --> create role.
step 2:
Name of the Authorization object is s_rs_comp
step 3:
Add the s_rs_comp1 to add user details.
Add the s_rs_comp1 to add user details.
Step 4: save and generate profile similar like ECC system.

























No comments:
Post a Comment